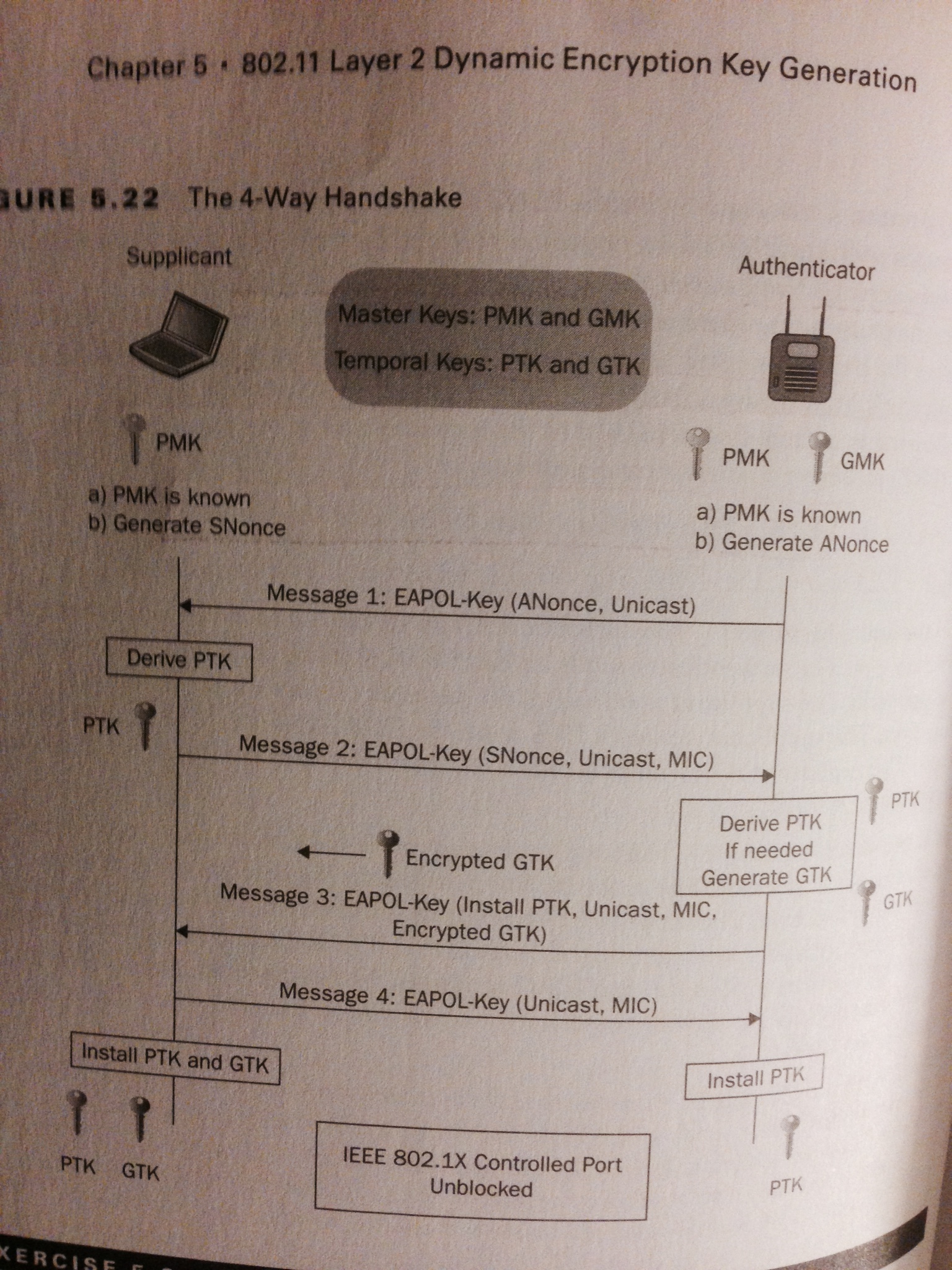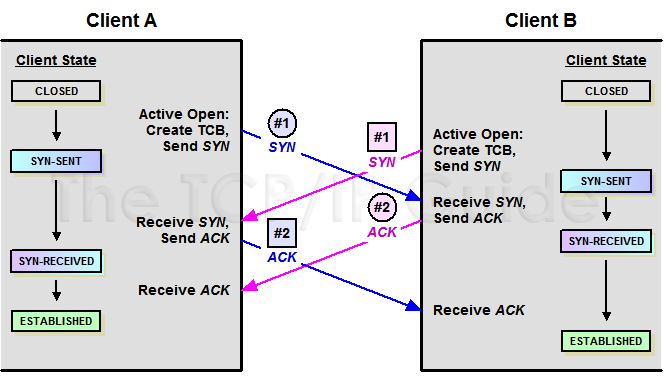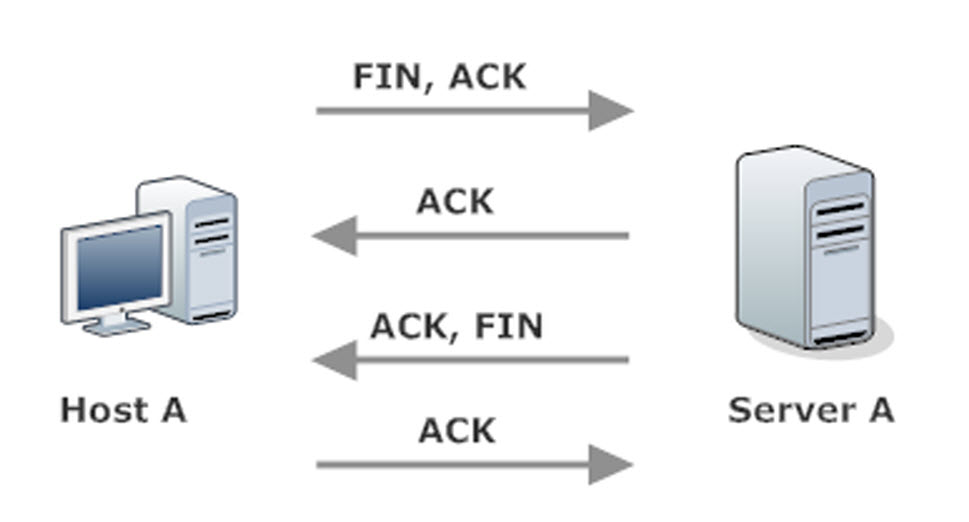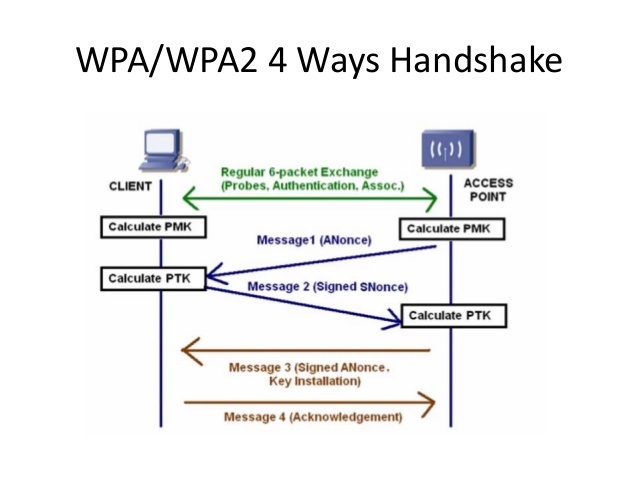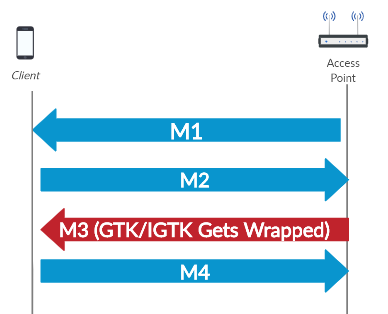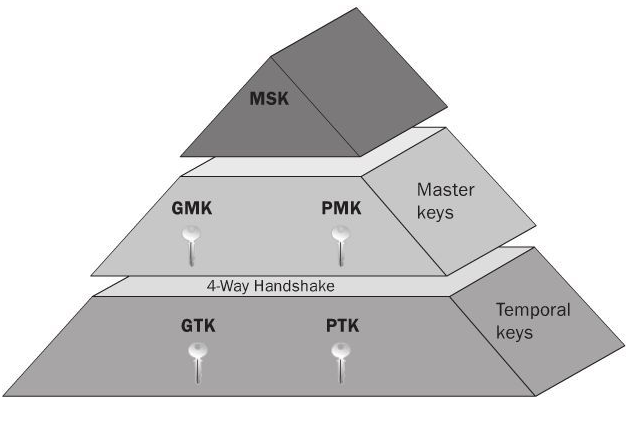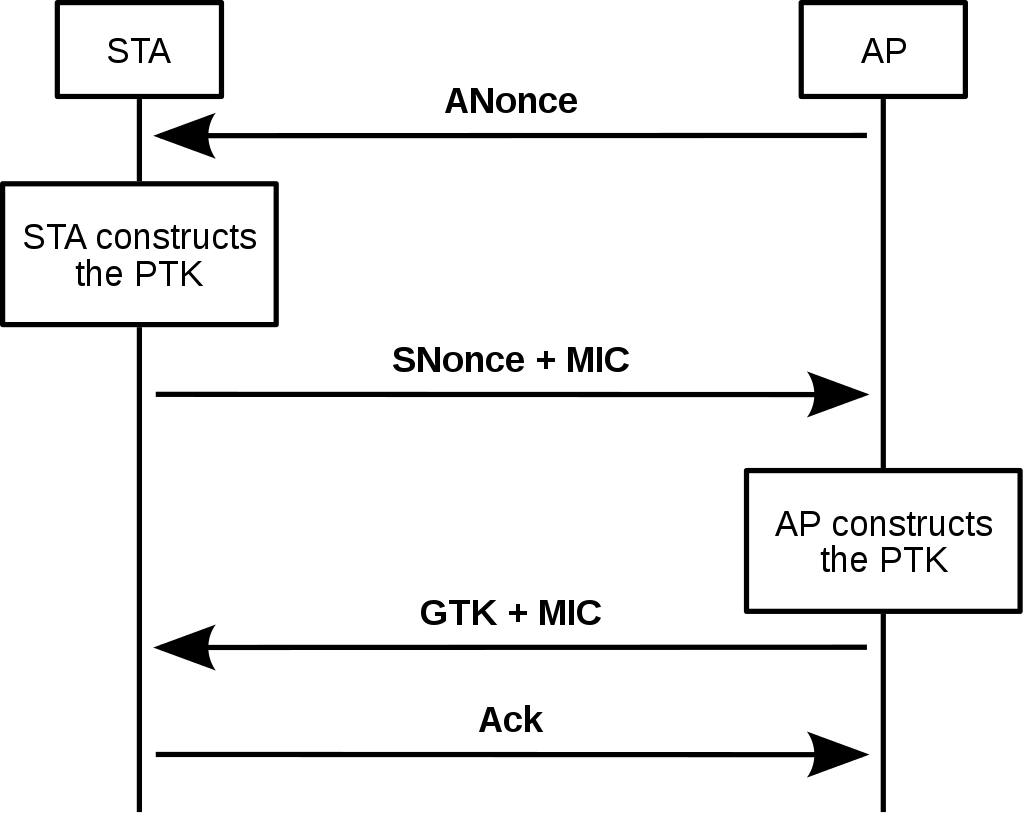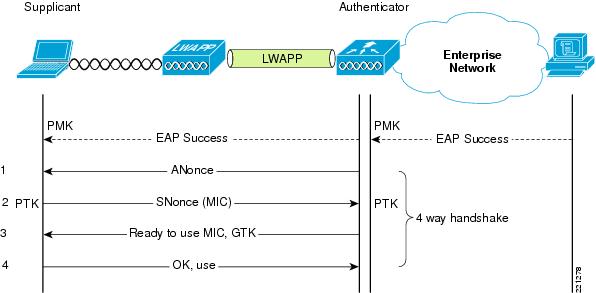
my80211.com - 802.1X LABS - GEORGE STEFANICK - CWSP JOURNEY, (CHAPTER 5 – 4- WAY HANDSHAKE POST#5)- 10/03/2010
Secure Authentication and Four-Way Handshake Scheme for Protected Individual Communication in Public Wi-Fi Networks
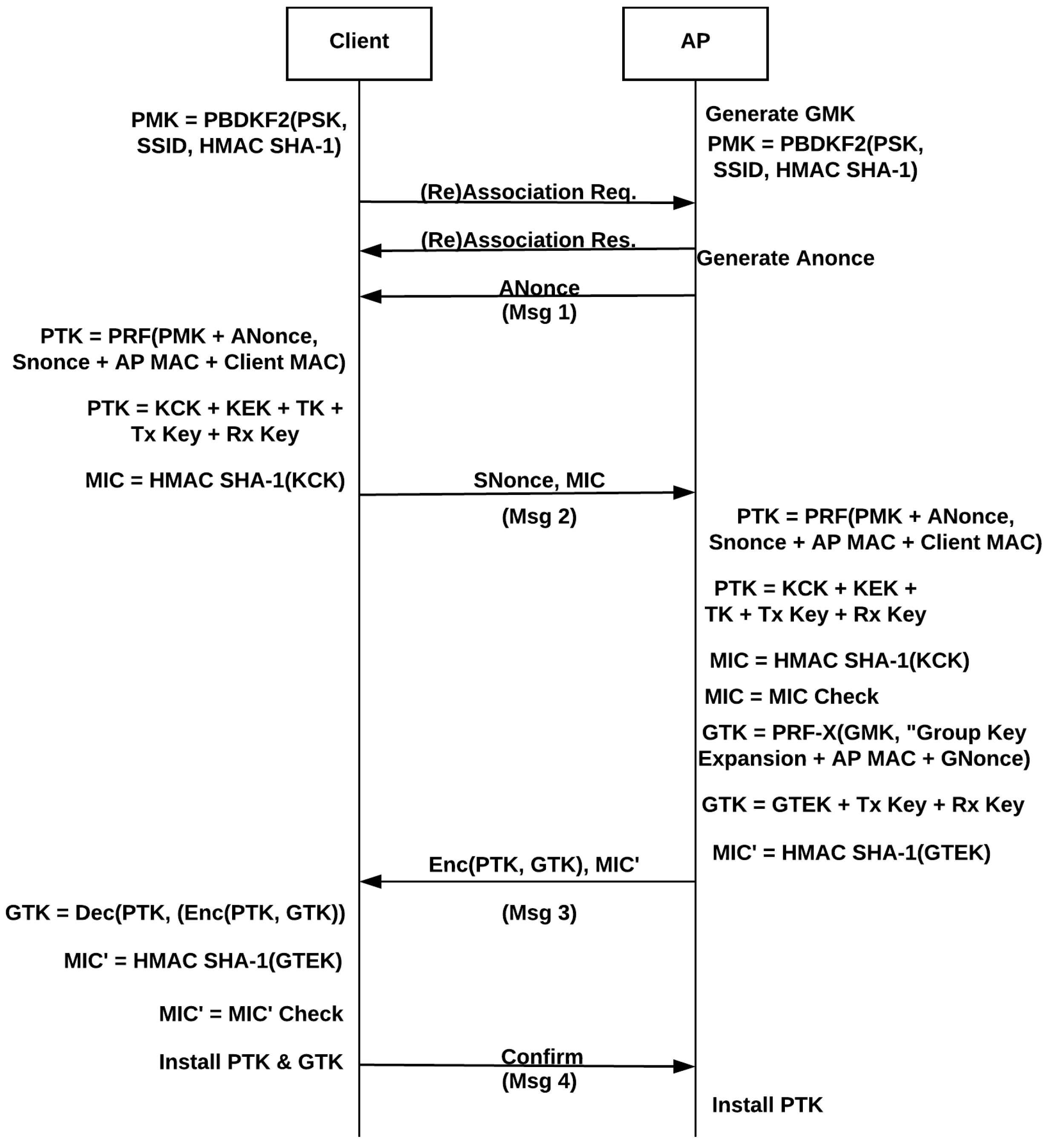
Electronics | Free Full-Text | A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3